
Multi-Factor Authentication
The two major shortcomings of passwords are:
- They can be easily stolen through phishing emails, logging keystrokes, etc. if users are not careful.
- Weak passwords can be easily guessed throughpassword spraying, dictionary attacks, etc.
In both cases, the attacker can obtain the user's password. But what if there's another authentication process that the attacker can't get hold of, like your fingerprints? Adding a second layer of authentication that only the true user can genuinely provide ensures that even if the first layer is compromised, the attacker can't get through the second layer.
Why can't we use just one strong authentication method, and make things easier? After all, it is extremely difficult to obtain someone's fingerprints, right? To answer this question, let's examine the three types of authentication factors.
Passwords fall under what are called knowledge-based factors, as you use something that only you know (hopefully) to confirm your identity. PINs and secret questions also fall under this category.
Then, you have inheritance factors. These are factors such as your fingerprints, eye retinas, DNA, which are things that you "inherit" and are part of your human body.
Lastly, there are possession factors. These are things authentication obtained from something you have with you, such as a key cards, a trusted smartphone, etc.
Each of these factors have their own set of shortcomings when used individually. For example, knowledge factors are compromised when someone else gains the knowledge. Possession factors are compromised when the trusted devices are stolen. Inheritance factors such as fingerprints, although extremely challenging to compromise, cannot possibly be changed once they are not secure anymore. However, when two or more of these factors are used together, one of the factors covers the other's shortcomings and vice versa, giving you a much stronger authentication system. For example, you can combine a knowledge-based factor, such as a password, with a possession factor, such as a code obtained from your smartphone. This way, if the smartphone is stolen, or if the password is obtained through phishing, one can't be used without the other to gain access to an account. Using MFA is an efficient way to prevent a data breach, or fall victim to attackers and their grand schemes.
Insurance providers are actively working towards applying controls, especially in terms of endpoint and weak password vulnerabilities, which can also help in disaster recovery. As you can see in the image below, the adoption of MFA has grown strongly (65%) in response to the popularity of automated credential-stuffing cyber attacks. More than 70% of SMBs have adopted endpoint detection and response measures. While username-password authentication remains the most popular security measure (93%), EDR and MFA adoption is likely to incrementally replace passwords in years to come.
Earlier, insurance renewal applications for cyber liabilities were fairly straightforward for both insurance vendors and buyers. The processes required minimal consumer information. However, with the evolution of cyber attacks, organizations must remain vigilant about changing trends from underwriters and adopt innovative security measures to keep their businesses running in a highly competitive environment.
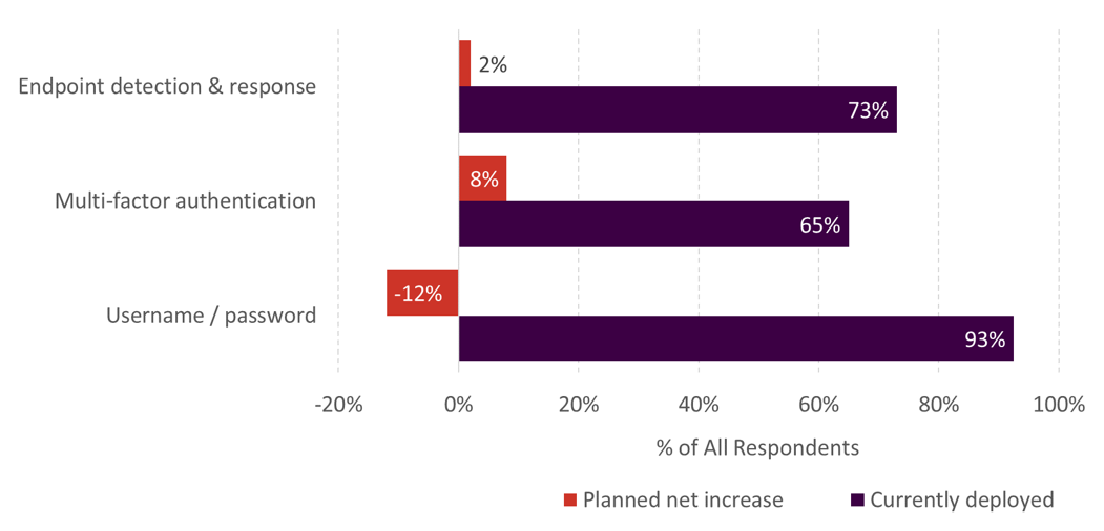
Rise in MFA and EDR Adoption by SMBs
Source: Aberdeen Strategy & Research
Works Cited:
ManageEngine. (n.d.). Multi-factor authentication. Multi-factor authentication | Identity and Access Management Solution - AD360. https://www.manageengine.com/active-directory-360/manage-and-protect-identities/multi-factor-authentication.html?mesearch
Mudaliar, A. (Ed.). (2023, January 19). Why are EDR & MFA important for Cyber Insurance Companies?. Spiceworks. https://www.spiceworks.com/it-security/cyber-risk-management/articles/edr-mfa-cyber-insurance-solutions/


