
Endpoint Detect and Response
What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is a cybersecurity approach that focuses on detecting and investigating security incidents on endpoints like desktops, laptops, servers, and mobile devices. EDR solutions collect and analyze endpoint data, network traffic, and user behavior to detect anomalous activities that could indicate a security breach.
EDR solutions are designed to provide real-time threat intelligence, automated incident response, and forensic investigation capabilities. EDR tools allow security teams to detect and respond to advanced threats quickly and efficiently, minimizing the risk of data breaches and other cybersecurity incidents.
Why is Endpoint Detection and Response (EDR) Important?
Endpoint security is critical for modern organizations, as endpoints are often the entry points for cybercriminals to infiltrate an organization’s network. Cyberattacks like malware, ransomware, and phishing attacks often target endpoints to gain access to sensitive data or to launch further attacks.
EDR solutions play a crucial role in endpoint security by providing real-time threat detection and response capabilities. With EDR tools, organizations can quickly identify and investigate security incidents, reducing the time to detect and respond to threats. This minimizes the impact of cyberattacks and helps organizations to recover from security incidents faster.
How to Enhance Endpoint Security with EDR Solutions
You need to follow a few best practices to enhance your endpoint security with EDR solutions. Here are some essential steps to implement EDR effectively:
Step 1: Choose the Right EDR Solution
When selecting an EDR solution, consider your organization’s needs and requirements. Look for an EDR solution that offers real-time threat detection, automated incident response, and forensic investigation capabilities. The solution should also be easy to use and integrate with your existing security tools and processes.
Step 2: Implement Best Practices for Endpoint Security
You should follow best practices for endpoint security to get the most out of your EDR solution. This includes implementing robust antivirus and anti-malware solutions, keeping the software and operating systems up-to-date, and enforcing strong password policies.
Step 3: Monitor Endpoint Activity and Network Traffic
EDR solutions collect and analyze endpoint data and network traffic to detect security incidents. To ensure that your EDR solution is effective, you must continuously monitor endpoint activity and network traffic. This will help you identify anomalous activities and potential security threats.
Step 4: Automate Incident Response
EDR solutions can automate incident response processes, reducing the time to detect and respond to security incidents. When a potential threat is detected, the EDR solution should automatically initiate incident response workflows, such as isolating the affected endpoint, blocking malicious traffic, and alerting security teams.
Step 5: Conduct Regular Endpoint Assessments
Regular endpoint assessments are crucial to ensure your EDR solution works effectively. Conduct regular security assessments to identify vulnerabilities and weaknesses in your endpoint security, and use the findings to improve your EDR solution.
How Insurance Providers Bolster the Adoption of MFA and EDR
With these requirements gaining prevalence, policy vendors are pushing buyers to improve cyber security setups. For organizations to get better insurance policies, they will now have to reduce the risk to the underwriters.
Insurance providers are actively working towards applying controls, especially in terms of endpoint and weak password vulnerabilities, which can also help in disaster recovery. Endpoint detection and response systems have gradually started to replace conventional antivirus solutions. These solutions surpass basic signature-based solutions, with the ability to isolate or shut down infected devices, halt processes, and remove suspicious files.
As you can see in the image above, the adoption of MFA has grown strongly (65%) in response to the popularity of automated credential-stuffing cyber-attacks. More than 70% of SMBs have adopted endpoint detection and response measures. While username-password authentication remains the most popular security measure (93%), EDR and MFA adoption is likely to incrementally replace passwords in years to come.
Earlier, insurance renewal applications for cyber liabilities were fairly straightforward for both insurance vendors and buyers. The processes required minimal consumer information. However, with the evolution of cyber-attacks, organizations must remain vigilant about changing trends from underwriters and adopt innovative security measures to keep their businesses running in a highly competitive environment.
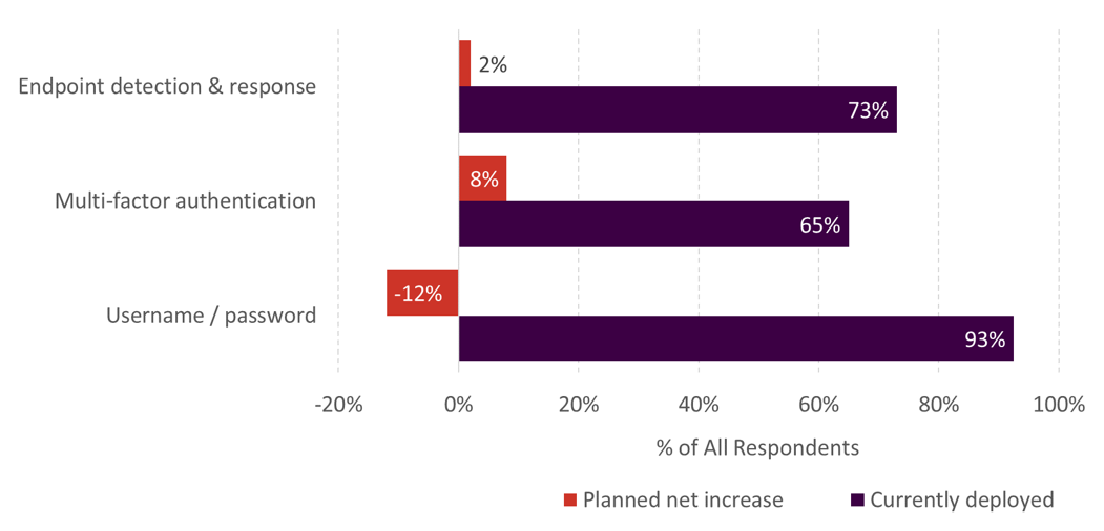
Rise in MFA and EDR Adoption by SMBs
Source: Aberdeen Strategy & Research
Works Cited:
SentinelOne. (2023, April 18). What is endpoint detection and response (EDR)?. SentinelOne. https://www.sentinelone.com/cybersecurity-101/what-is-endpoint-detection-and-response-edr/
The World Has Changed. Has Your Cybersecurity? (n.d.). SentinelOne. Retrieved June 12, 2023, from https://www.sentinelone.com/resources/the-world-has-changed-has-your-cybersecurity/.
Mudaliar, A. (Ed.). (2023, January 19). Why are EDR & MFA important for Cyber Insurance Companies?. Spiceworks. https://www.spiceworks.com/it-security/cyber-risk-management/articles/edr-mfa-cyber-insurance-solutions/


